Spamming/Phishing analysis

I just get a mail today, flagged as spam in my mailbox. As I didn’t have much to do today, I decided to have a look at it, and check what was the goal of the spammer. First let’s have a glance of what is spamming and phishing. Spam is the use of electronic messaging […]
MITM 8: Countermeasures
March 4, 2012

There are two main kinds of countermeasures for the ARP poisoning and the man-in-the-middle attack in general. The first is the prevention and the second is detection. Prevention try to avoid an attacker while detection trigger an alarm when it notices that looks like an attack or the result of an attack. To ensure a […]
MITM 7: Sniffing with TCPDump
February 25, 2012
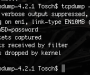
I’ve been thinking about whether develop a new application — and reinvent the wheel like for ARP poisoning with libnet and libpcap — or using tools already available. I finally decided to use TCPDump because this tool might be really handy in many situations. I think I will improve ARP Spoof SI anyway with a […]
MITM 6: ARP spoofing (exploit – 2)
February 21, 2012

Today we are gonna reinvent the wheel, and the worst part is that we won’t even improve it. Why? Because I want to develop an ARP spoofer in C from the scratch based on what we’ve learnt so far in this tutorial. For this program, I used the multi-platform libraries libnet (for forging packets) and […]
MITM 5: Forwarding packets
January 31, 2012

As mentioned in the previous post, after spoofing the ARP table of both victim and default gateway, you may block the internet connection of the victim because packets are sent to the attacker which doesn’t forward them to the default gateway: the attacker open the packet (data link layer) and read the destination IP address […]
MITM 4: ARP spoofing (exploit)
January 31, 2012

Now I described how ARP works, let’s exploit the weakness: deceiving the victim and the default gateway by pretending to be both of them. There are many tools for the ARP spoofing such as Cain & Abel, Ettercap and DSniff (I will soon write a tutorial about Ettercap and Cain & Abel). In order to […]
OSI model – Layer 4: Transport (TCP and UDP with Scapy)
January 30, 2012

I already wrote an article describing the OSI model and its 3 first layers (physical, data link and network). Now I’ll talk about the layer 4: transport. While the data link layer carries the point-to-point connections and the network layer carries the routing of packets, the transport provides end-to-end communication services for applications. The transport […]
Scapy – Decode and forge your own packet
January 24, 2012

I started to write articles on the wiki of Sec IT’s related to the posts on this blog. If you want to modify or improve the articles (I’m pretty sure there are plenty of typos and materials to describe), feel free to edit it on the wiki. Scapy is an application for packet manipulation written in […]


March 15, 2012
2